Background
Historically enterprises had been content with having a single public cloud provider. But as business requirements have evolved with the desire to reduce single-vendor lock-in and the need for increased resiliency, multicloud setups are becoming the new norm. This has been confirmed by Oracle’s recent survey which identified three main factors driving multicloud adoption:
- Data sovereignty and locality
- Cost optimization and
- Business agility and innovation
However, multicloud also comes with its own set of challenges. It is difficult to manage credentials safely for human and non-human users, hard to prevent escalation of privilege or backdoor access, apply uniform policies across a fleet of accounts for governance and gain visibility into the cloud workloads, security issues and cost.
Here are some examples of account misconfigurations that have resulted in data breaches and damaged business reputations in recent years. Account misconfigurations refer to errors made during the deployment or maintenance of cloud-based platforms or applications. In addition to exposing security gaps, misconfiguration can also lead to cost overruns.

In the diagram above, we see cloud configuration errors leading to breaches in CapitalOne, HobbyLobby, Toyota and National Public Data. Palo Alto networks’ report highlights how malicious actors can use cloud misconfigurations for ransomware and extortion. The IBM report puts the cost of a breach at around $4.8 million.
How to prevent these attacks?
To prevent these attacks, multiple steps need to be implemented. The critical ones being:
Access Credential Management:
In public cloud usage, access credentials are utilized by both human and non-human entities. The credentials are used to gain access to the public cloud resources or do operations on them. Typically, non-human identities used for workflows outnumber human identities by 1:9 to up to 1:20 or more. Most of the time, the access credentials are static, needing manual rotation or change. When there are large number of accounts, static credentials become problematic as people forget to rotate them. Using short lived ephemeral credentials for access is the answer for all identities whether through federation with an existing Identity Provider (IdP) or without one. This eliminates the need to manage the credentials securely.
Least Privilege Principle:
From a security viewpoint, it is preferable to utilize the least privileged access to accomplish tasks. As an example, to view spend or see what resources are used, read-only access should suffice.
Secure Configuration:
The cloud resources can be configured using governance policies across a fleet to enforce uniformity. As an example, it may be desirable to enforce a default retention period on S3 buckets on an AWS account fleet for governance and cost optimization purposes. Similar configurations can be enabled on Azure Blob Storage or Google Cloud Storage.
This can be accomplished with the use of governance policies that make sure the policies remain in place for the entire fleet as accounts are added or deleted, and when there is configuration drift.
Monitoring and Logging:
Monitoring and logging are crucial components of cloud infrastructure management. It enables an organization to (a) determine security threats in real time (b) troubleshooting and incidence response (c) compliance and auditing and (d) provides visibility and transparency for the engineering teams.
An organization may want to configure the logs (retention period, access) uniformly across the accounts in one or more clouds.
Visibility:
In addition to the visibility provided by logs, it is important to have a cloud agnostic tagging system to identify the owner, manager, security, FinOps contact for an account. This is typically done at account creation time. It enables quick communication with the relevant person when there are issues or questions regarding a specific account.
Regular audits:
Many industries require comprehensive activity logs for regulatory compliance. In addition, conducting regular penetration testing to identify security vulnerabilities is considered a best practice.
Strato Cloud Solutions
Strato Cloud is the only company that is providing a solution for multicloud access, governance while providing visibility in a wholistic way. Strato Cloud provides the ability to an organization to implement the controls mentioned above and more in a flexible manner. Strato Cloud believes that security needs to be implemented at the account/project/subscription level to all the cloud resources uniformly.
Access Credential Management:
Strato Cloud provides short-lived ephemeral access credentials and granular access controls to both human and non-human users. This prevents a slew of attacks stemming from credential leakage, unauthorized access and account hijacking. Just-in-time access is enabled through the API as well as the UI. Strato Cloud applies permission boundaries to certain roles so new identities can’t be created without proper review and approvals.
Least privilege:
Granular controls allow access with the least privilege needed to do the work. As an example, a person looking at cost can check the accounts with read-only access whereas an engineer that needs to do rotate or recycle VMs may need power user access. Strato Cloud allows different personas to have the right level of access to do their work.
Secure Configuration:
Strato Cloud allows custom governance policies to be built and deployed across a fleet of accounts. The governance policies can be implemented using Infrastructure as Code (IaC) of one’s choice and deployed centrally in a repeatable way.
Monitoring and Logging:
Monitoring and logging can be enabled in an account using governance policy packages. These are typically enabled using IaC of one’s choice, built as a package and deployed to a fleet of accounts.
Strato Cloud access and governance together prevent some of the common misconfiguration patterns noted by acqua security such as (a) overly permissible access to workloads (b) back-ups that aren’t properly secured (c) exposed access keys (d) unrestricted inbound/outbound ports (e) proper monitoring, logging and configuration of alerts.
Visibility:
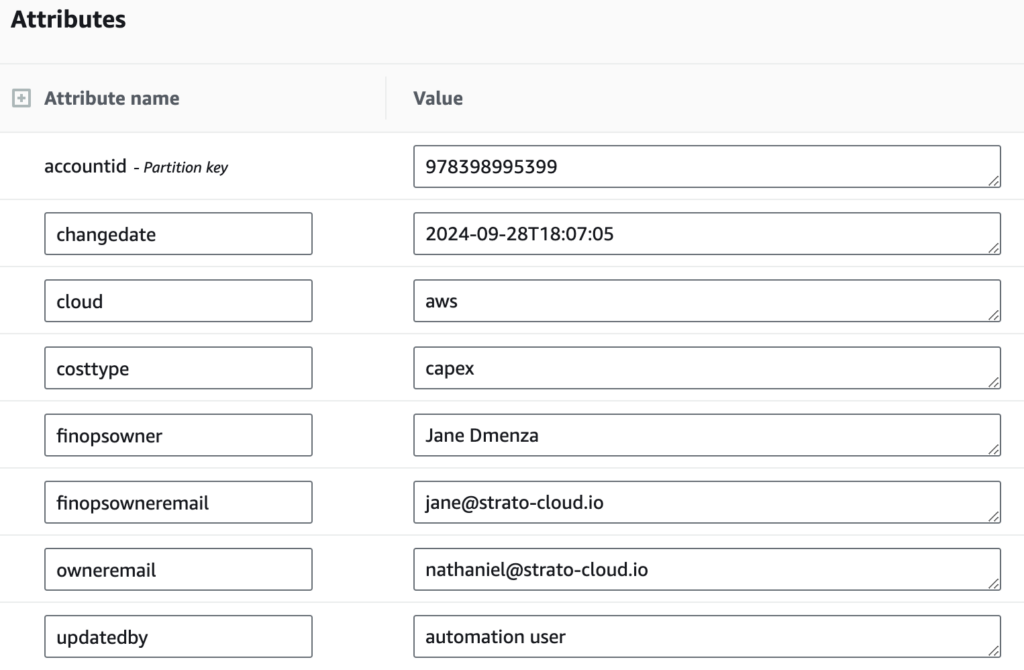
Strato Cloud enables visibility at an account level in a cloud agnostic way. The attributes are fully customizable by an organization and typical account attributes look as shown in the below picture. This is typically done at account creation time using account lifecycle management service from Strato Cloud. Strato Cloud also provides visibility to security issues, and cloud spend.
Regular audits:
Strato Cloud governance packages make auditing an easy and seamless process. The logging controls can be used for SOC2, PCI and ISO compliance.
Sign up today!
To sign up and explore the offers available at Strato Cloud, you can visit our website at strato-cloud.io. If there are further questions or need further assistance, we can be reached via email at info@strato-cloud.io

